This was a quite easy but fun challenge.
It’s about extracting data from a pcap file with SIP communication captured.
If we take a look at the .pcap we see some SIP communication which can be easily inspected via the setting “Telephonie” in Wireshark. With that, we can see that there are two calls and one of them got rejected. So we are interested in the successful/ completed call.
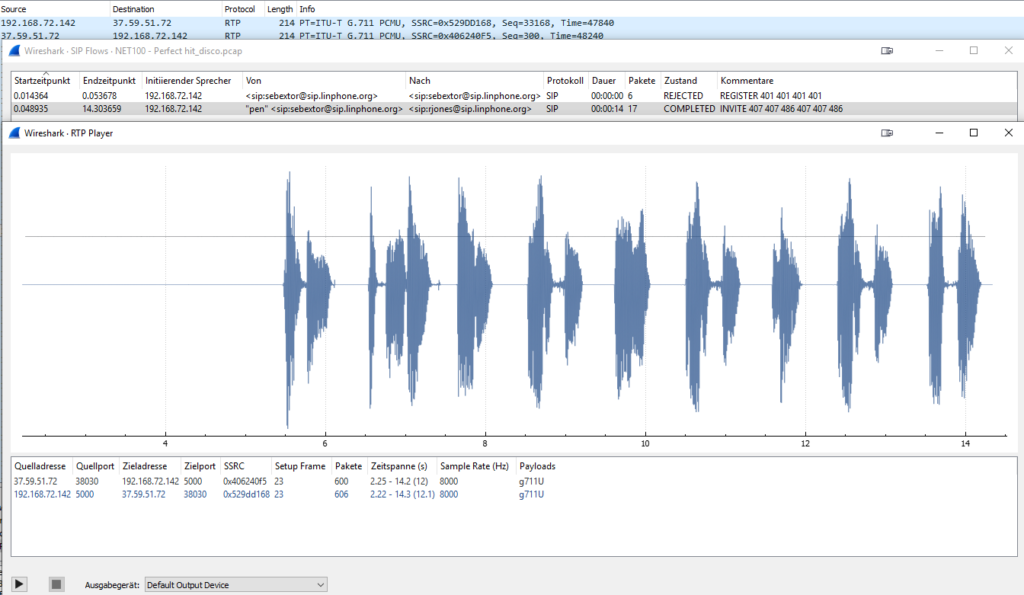
After playing the stream we get the first flag. But that’s not it because this challenge has two flags hidden. So let’s take a look for the password which is the next topic of interest and should be somewhere at the registration or contact phase of both participants.
After inspecting the traffic we see some unauthorized requests and after that a request with REGISTER and after that a status 200 with all the required information.
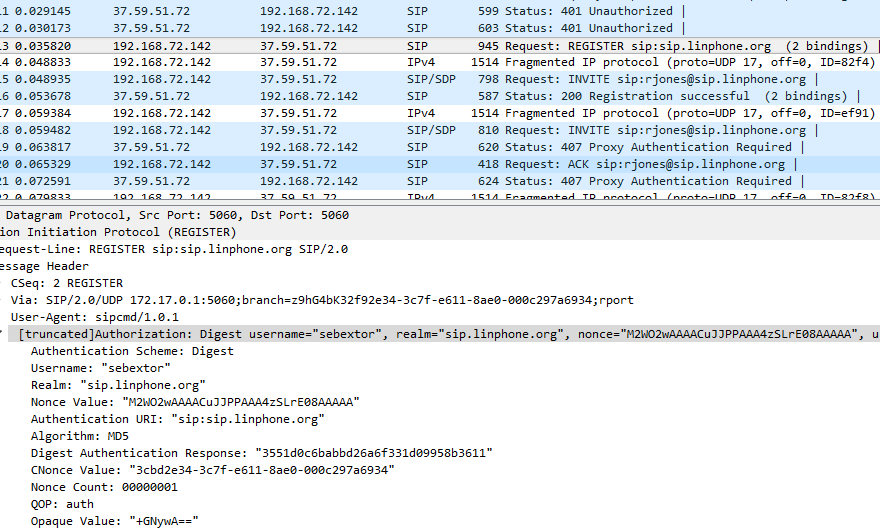
But what to do now with interesting information. Just use the SIPcrack 0.2 tool on Kali Linux and let it crack the password for you. But SIPcrack requires a sipdump file and we just got a pcap.. :/
Just use the SIPdimp tool to extract the relevant information from the .pcap and transform the found data into a sipdump file via:
sipdump -p '/root/Downloads/disco.pcap' ./sipFile
* Using pcap file '/root/Downloads/disco.pcap' for sniffing
* Starting to sniff with packet filter 'tcp or udp'
* Dumped login from 37.59.51.72 -> 192.168.72.142 (User: 'sebextor')
* Dumped login from 37.59.51.72 -> 192.168.72.142 (User: 'sebextor')
* Dumped login from 37.59.51.72 -> 192.168.72.142 (User: 'sebextor')
* Dumped login from 37.59.51.72 -> 192.168.72.142 (User: 'sebextor')
* Exiting, sniffed 4 loginsFollowed by the SIPcrack tools and your done!
sipcrack -w /usr/share/wordlists/rockyou.txt ./sipFile
* Found Accounts:
Num Server Client User Hash|Password
1 192.168.72.142 37.59.51.72 sebextor 3551d0c6babbd26a6f331d09958b3611
2 192.168.72.142 37.59.51.72 sebextor ea6ca2158821cd4357e91a7290c614fe
3 192.168.72.142 37.59.51.72 sebextor b991929ad456f72b9918a28e8e51947e
4 192.168.72.142 37.59.51.72 sebextor 30c66e99d569039044054906da7e68fe
* Select which entry to crack (1 - 4): 2
* Generating static MD5 hash... d845bafc8c359f2d392f2fd2eb11b083
* Loaded wordlist: '/usr/share/wordlists/rockyou.txt'
* Starting bruteforce against user 'sebextor' (MD5: 'ea6ca2158821cd4357e91a7290c614fe')
* Tried 7476821 passwords in 3 seconds Weitere Posts zum Thema Web-Security und Penetration-Testing
NET100 – Perfect hit
This was a quite easy but fun challenge.It’s about extracting data from a pcap file with SIP communication captured. If we take a look at the .pcap we see some SIP communication which can be easily inspected via the setting “Telephonie” in Wireshark. With that, we can see that there are two calls and one…
WEB100 – XXE Denial of Service
This challenge was the usual XXE attack called entity injection with the goal to crash the server. This reminded me of the old but good billion laughs attack. With this attack, your recursive include entities which include further entities to overload the RAM of the XML parser and crash the program.To execute the attack we…
MSC100 – Base32
MSC100 – Base32 This one was harder for me. Made some bad mistakes at the beginning which really left me clueless. The description was that someone encrypted text with base32 but did something wrong. So I tried to decrypt it with some online decoders but they all went crazy because of characters which are not…
WEB200 – The rocket clock
This challenge was a web challenge. A PHP code to inspect and to tell what’s the problem with it and then exploit the weakness in the servers running this application. At first, I tried to take a look at the input which is controlled by the user. This is where we can manipulate and send…

Penetration Test Report ISIS12
Dieser Penetration Test wurde durchgeführt von Patrick Eisenschmidt. Inhaltsverzeichnis Timeline Dokumentenversion 1. Einführung 2. Technische Umgebung und Randbedingungen 3. Kategorisierung der Schwachstellen 4. Findings 4.1. XSS (Cross Site Scripting) 4.2. Benutzung eines schwachen Algorithmus zur Berechnung von Kennwort-Hashes Timeline Zeit Beschreibung 08.01.2019 Bericht an den Ansprechpartner der Hochschule gesendet 09.01.2019 Bericht wurde an den Hersteller…

Untersuchung der Kommunikation der App UniNow
Die Kommunikation der App UniNow wurde von Patrick Eisenschmidt auf personenbezogenen / datenschutzrelevante Daten geprüft. Dein ganzes Studium immer dabei. Mit UniNow hast du alle wichtigen Informationen rund um dein Studium in nur einer App! Egal ob Noten, deine Mails oder deinen Stundenplan – du hast alles immer und überall dabei! Inhaltsverzeichnis Dokumentenversion 1. Einführung…
CRY100 – Decrypt this text
This challenges is about decrypting the text inside a file. At first, it does not pretty good. Most characters are not printable or just jibberish.Sadly I can’t remember correctly what the description said (have to write it down next time) but I guess something about the text is XOR’d and the key has to be…
